DRAGOS CTF 2023
After some easy trivia challenges in the DRAGOS 2023 CTF, the first 200 points challenge, called “Global Session planning” was a stegano challenge. I provide below just a focus on a flag hidden in the JPG file only in one of the first easy challenges.
Attached to the challenge was provided a “manekineko.jpg” accompanied with below text:
After trying most of the “usual easy tools” to retrieve a flag in a steganography challenge :
- strings : no strings of interest
- exiftool : no flag
- binwalk : no file included
- metadata : no metadata
- change of colors, gradient, error level analysis….etc : nothing
- …etc)
- jsteg was also unsucessful
#https://github.com/lukechampine/jsteg/ ─$ jsteg reveal manekineko.jpg could not decode jpeg:unsupported JPEG feature: progressive decoding
I finally used outguess-extract and got an interesting clue as below:
outguess-extract manekineko.jpg test.jpg Reading manekineko.jpg.... Corrupt JPEG data: 8332 extraneous bytes before marker 0xc4
Having an “extraneous bytes before marker” was a sign that the probable technique used was a change of size of the picture !
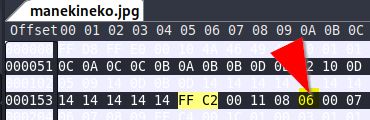
Based on some links from cyberhacktics and hackmd.io I got the tip to edit the JPG Height starting at the FFC2 marker.
On kali I used the practical wxhexEditor and updated the first byte for the height (04 to 06)
We play with the initial height (just after the “Data precision ” byte) :
It was then easy to to visualize the flag as flag{not_everything_is_as_it_seems}.
It is interesting to note that the initial marker pointed 0xC4 is DHT 0xFF, 0xC4 variable size Define Huffman Table(s) Specifies one or more Huffman tables.