Information Security models (security architecture implementation models)
Franck Jeannot – July 2023 – ref P460.
Keywords: Security models, Access control matrix, Biba, Bell-LaPadula, Brewer and Nash (Chinese Wall), Clark-Wilson, Graham-Denning, Goguen-Meseguer, Harrisson-Ruzzo-Ullman, Information fow, Noninterference model, State machine, Sutherland, Take-Grant
Some important architecture implementation security models: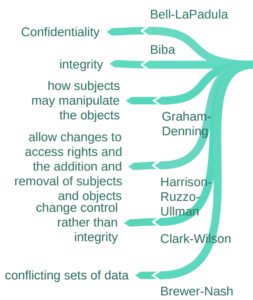
Fig (1) : Examples of architecture security implementation models
1 – Lampson access-control model (1971). Abstract, formal security model of protection state in computer systems. It characterizes the rights of each subject with respect to every object in the system 1. This model is also known as the access control matrix or access matrix.
2 – Graham-Denning Model (1972): This model provides a set of basic operations for managing subjects and objects. The model is based on the Access Control Matrix model, where rows correspond to subjects and columns correspond to objects and subjects. Each element in the matrix contains a set of rights between subject i and object j or between subject i and subject k.
3 – Bell-LaPadula Confidentiality Model (BLP)(1973): This model is focused on maintaining the confidentiality of information. It uses two main rules: the Simple Security Property (no read up, no write down) and the *-Property (no write up, no read down). MNENMO: Bell-LaPadula Model (BLP): “Bell rings high, secrets lie low” – This phrase helps remember that in BLP, you can’t read up (higher classification) or write down (lower classification).
4 – State Machine Model (BLP and others, 1973)
The state machine model is based on a finite state machine. State machines are used to model complex systems and deals with acceptors, recognizers, state variables, and transaction functions. The state machine defines the behavior of a finite number of states, the transitions between those states, and actions that can occur.
5 – Biba Model (1975): This model is designed to maintain the integrity of information. It uses two main rules: the Simple Integrity Property (no read down, no write up) and the *-Integrity Property (no write down, no read up). MNENMO: “Biba’s book integrity, no low read or high deed” – This phrase helps remember that in the Biba model, you can’t read down (lower integrity) or write up (higher integrity).
The Bell-LaPadula model is defined by the following properties:
- Simple security property (ss property)—This property states that a subject at one level of confidentiality is not allowed to read information at a higher level of confidentiality. This is sometimes referred to as “no read up.”
- Star * security property—This property states that a subject at one level of confidentiality is not allowed to write information to a lower level of confidentiality. This is also known as “no write down.”
- Strong star * property—This property states that a subject cannot read/write to object of higher/lower sensitivity.
6 – Harrison-Ruzzo-Ullman (1976) (HRU) Model: It is a discretionary access control model that deals with the integrity of access rights in a system. This model is used to determine if a certain access right can be safely granted.
7 – Take-Grant Model (Lipton, Richard J and Snyder, Lawrence, 1977): This model is used for or analyzing the rights and permissions that can be acquired during the operation of a system. It provides a framework for evaluating the flow of privileges between subjects and objects within a system. By examining the take and grant operations, this model helps identify potential vulnerabilities and access control issues in a system.
8 – Lipner model (Steve Lipner (Microsoft) (Biba-BLP Model)– combines the Bell-LaPadula and Biba models to enforce confidentiality and integrity in information systems. It uses security levels to control information flow and integrity levels to prevent unauthorized modifications. The Lipner Model is the first commercially successful security model. Lipner developed a hybrid policy using both BLP and Biba’s Strict Integrity to address commercial integrity concerns.
9 – Information Flow model (1976-1982) In the field of computer security, one of the earliest and most influential Information Flow models was introduced by Denning in 1976. In the field of computer security, Information Flow security models are used to analyze and control the flow of information within a system to prevent unauthorized disclosure or modification of sensitive data. One of the earliest and most influential Information Flow security models is the Noninterference model, introduced by Goguen and Meseguer in 1982
10 – Non-Interference Model (Goguen & Messeguer (1982)) This model is designed to prevent actions at a high security level from impacting objects at a lower security level.
11 – Sutherland (1986) Sutherland’s Nondeducibility Model ( Based on Information Flow). This model states that information
flows in a system from high-level objects to low-level objects if and only if some possible assignment of values to the low-level objects in the state is incompatible with a possible assignment of values to the state’s high-level objects. (ref ‘‘A Model of Information,’’ in Proc. of the 9th National Computer Security Conference, Gaithersburg, MD., September, 1986)
12 – Clark-Wilson Model (1987-1989): This model is also focused on maintaining the integrity of information. It uses well-formed transaction and separation of duties concepts.
13 – Brewer-Nash Model (1989) (A.K.A Chinese wall model) : This model is designed to maintain the confidentiality of information. It prevents a user who has legitimate access to data from using that data in a way that could negatively impact the business.
Ref 1: https://www.sunflower-cissp.com/downloads/sunflower_cissp_layout.pdf
Ref 2: https://coggle.it/diagram/WN9DIuqtdwABBohC/t/security-models
Ref 3 https://cdn.comparitech.com/wp-content/uploads/2020/01/CISSP-Cheat-Sheet-Domain-3.pdf
Mnemotechnic and synthesis table for the implementation security models
| Name | Type | Main concepts |
|---|---|---|
 BELL-Lapdula |
Confidentiality | Strong Star, no read up, no write down,Tranquility Property, MAC   |
 Biba Biba |
Integrity | No read down, no write up |
| Clark-wilson | Integrity | Well formed transactions, separation of duties, Transformation procedures, Verifications procedures (IVPs), Constrained Data Item (CDN), Constrained Interface |
| Lipner (BELL Lapdula + Biba) | Confidentiality and Integrity | BLP + BIBA |
| Guoguen-Meseguer | Integrity | Predetermined actions on predetermined objects |
 Brewer and Nash Brewer and Nash |
Conflict of Interests | Information Flow, Chinese wall, Separation fo Data, Dynamically chaining access controls |
| Graham Denning | Access Control Matrix, Read Grant Delete Transfer, 8 protection rights, Objects ahave owners | |
| HRU (Harrison, Ruzzo, Ullman) | Integrity | |
| Sutherland | Integrity | State machine, a state of states, state transitions |
