MetaRed TIC Ecuador was responsible for organizing the 5th stage of the MetaRed International CTF (Capture the Flag) 2023.
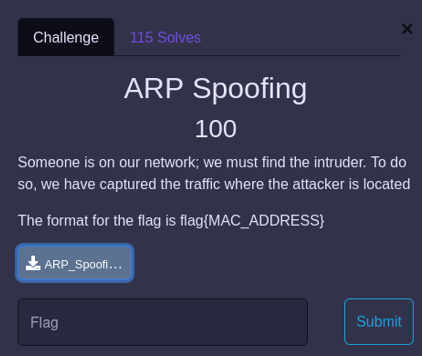
The first challenge, named “ARP Spoofing (100 points)” was providing the following clue : ” Someone is on our network; we must find the intruder. To do so, we have captured the traffic where the attacker is located. The format for the flag is flag{MAC_ADDRESS}” and a PCAP file “ARP_Spoofing.pcapng” was attached:
The first hypothesis was that there were duplicate IPs and MAC_ADDRESS. Having a look to a packtpub.com article , I found a Wireshark filter of interest, pointing to the fact that Wireshark can detects duplicate IPs in the ARP protocol. One have to use the arp.duplicate-address-frame Wireshark filter to display only duplicate IP information frames.
However the obvious potential duplicates and there relative were not successful FLAGS :
Knowing the filter in wireshark I was able to filter the file with tshark as below:
tshark -r ARP_Spoofing.pcapng -Y "arp" 187 52.600573 Cisco_bd:cb:c5 ? Broadcast ARP 60 Who has 172.18.4.122? Tell 172.18.4.1 190 53.073499 Dell_00:59:16 ? Broadcast ARP 60 Who has 172.17.187.157? Tell 172.18.4.155 193 54.170387 Dell_00:59:16 ? Broadcast ARP 60 Who has 172.17.186.235? Tell 172.18.4.155 194 54.720766 Cisco_bd:cb:c5 ? Broadcast ARP 60 Who has 172.18.4.122? Tell 172.18.4.1 201 57.164753 Cisco_bd:cb:c5 ? Broadcast ARP 60 Who has 172.18.4.122? Tell 172.18.4.1 202 57.347026 Dell_52:97:96 ? Broadcast ARP 42 Who has 172.18.4.1? Tell 172.18.4.173 (duplicate use of 172.18.4.173 detected!) 203 57.348099 Cisco_bd:cb:c5 ? Dell_52:97:96 ARP 60 172.18.4.1 is at 00:da:55:bd:cb:c5 (duplicate use of 172.18.4.173 detected!) 208 59.543526 Dell_00:59:16 ? Broadcast ARP 60 Who has 172.18.4.1? Tell 172.18.4.155 211 60.617134 Cisco_bd:cb:c5 ? Broadcast ARP 60 Who has 172.18.4.122? Tell 172.18.4.1
Other failed …FLAGS were the following:
flag{Dell_52:97:96}
flag{00:da:55:bd:cb:c5}
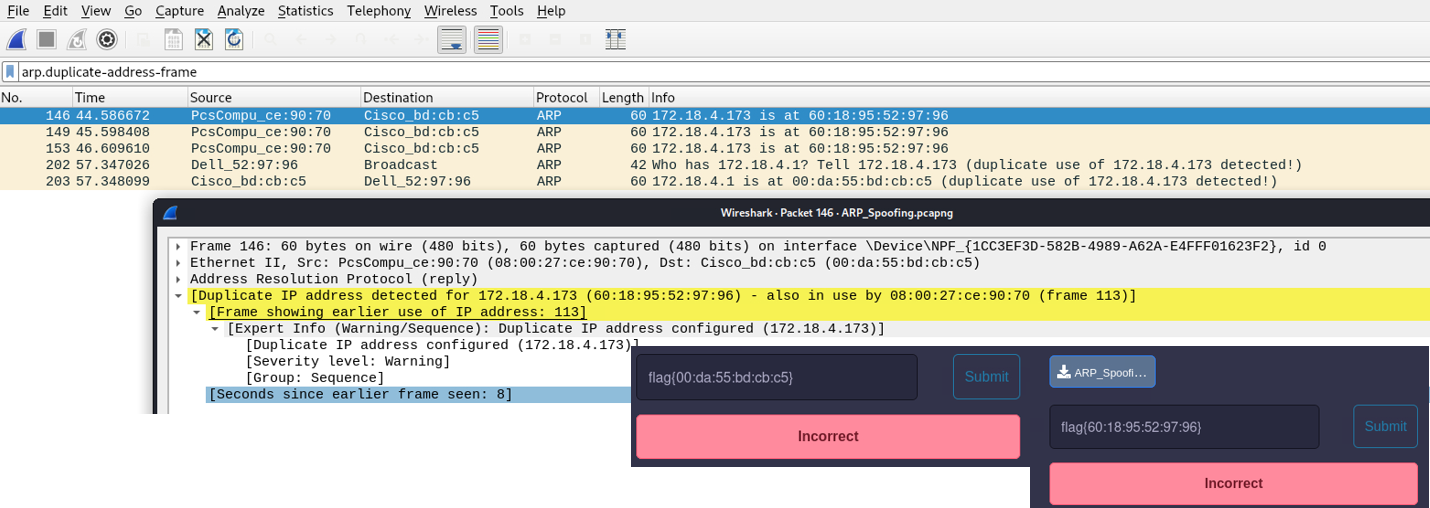
Finally having a closer look, Frame 146 is the targeted one 🙂
Frame 113: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface \Device\NPF_{1CC3EF3D-582B-4989-A62A-E4FFF01623F2}, id 0
Ethernet II, Src: PcsCompu_ce:90:70 (08:00:27:ce:90:70), Dst: Cisco_bd:cb:c5 (00:da:55:bd:cb:c5)
Address Resolution Protocol (reply
...
Frame 146: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface \Device\NPF_{1CC3EF3D-582B-4989-A62A-E4FFDDDDXXXX}, id 0
Ethernet II, Src: PcsCompu_ce:90:70 (08:00:27:ce:90:70), Dst: Cisco_bd:cb:c5 (00:da:55:bd:cb:c5)
Address Resolution Protocol (reply)
[Duplicate IP address detected for 172.18.4.173 (60:18:95:52:97:96) - also in use by 08:00:27:ce:90:70 (frame 113)]
[Frame showing earlier use of IP address: 113]
[Expert Info (Warning/Sequence): Duplicate IP address configured (172.18.4.173)]
[Duplicate IP address configured (172.18.4.173)]
[Severity level: Warning]
[Group: Sequence]
[Seconds since earlier frame seen: 8]
Confirmed successful FLAG (based on the destination MAC_ADDRESS in frame 146:
flag{08:00:27:ce:90:70}